
Network Address Translator (NAT) and its extension Network Address and Port Translator (NAPT) can expand the number of IP addresses available to an organization and can prevent users in the public network from becoming aware of some of the addresses in the private network. NAT works by using public IP addresses to represent private IP addresses.
Public IP addresses are the valid addresses of hosts in the IP public network and they must be unique within the public network. If the public network is the Internet, the public IP addresses must be unique Internet addresses provided by the Network Information Center (NIC).
The private addresses are known to the router, but not to the public network. The addresses within each private network must be unique; however, the same address can be duplicated in two different private networks. The private addresses are assigned to hosts within stub networks. Stub networks are networks that have access to the public network through one router only.
NAT expands the number of available IP addresses in several ways:
Using private addresses also hides these addresses from the outside world. This feature of NAT makes it useful as a type of firewall to protect the private addresses from being known.
| Important: | As stated in section 5.4 of the Internet Draft which defines NAT, "any application that carries (and uses) the IP address (and TCP/UDP port, in the case of NAPT) inside the application will not work through NAT...". It should be noted that DLSw and XTP make decisions based on the end-point IP addresses -- specifically which partner has the higher address. Since the application (such as DLSw or XTP) that is running through NAT thinks that its address is the private address, but the partner application in the other router thinks that the application's address is the public address, incorrect decisions can be made. |
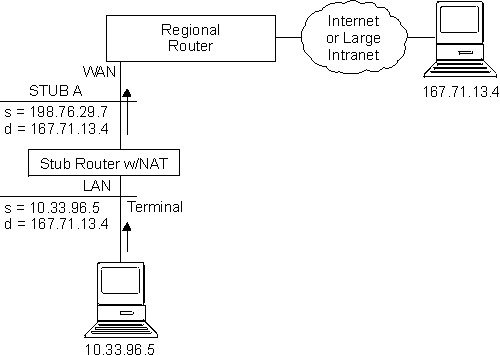
See Figure 44 for a drawing of a workstation in a stub network. In this example, the stub network consists of an IP subnet that has the IP address 10.33.96.0 with the subnet mask 255.255.255.0.
Figure 44. Network Running NAT

To use NAT, the network administrator assigns one or more public IP addresses to a public address pool in the 2212 and assigns a private IP address to each workstation in the stub network. The public IP addresses are assigned to a reserve pool and the private IP addresses are assigned to the translate range.
The NAT function first binds the private address of a station in the private network to one of the public addresses. Binding means that every packet with that private address will be translated to that public IP address when the packet is outbound. Inbound packets have the public IP address as their destination. NAT recognizes the public address, translates it to the private IP address, and forwards the packet. After traffic stops, the binding is maintained until a timer that you can set times out. At this time, NAT ends the binding and makes the public address available for reuse.
In this example, a packet is transmitted from sending private source address 10.33.96.5 to a destination address in the Internet, 167.71.13.4. NAT in the 2212 translates private address 10.33.96.5 to public address 198.76.29.7. This translation hides the private address 10.33.96.5 from the public network, so that no incoming packet is addressed directly to private address 10.33.96.5. Instead, incoming packets from 167.71.13.4 are addressed to public address 198.76.29.7. When the NAT router receives packets addressed to 198.76.29.7, NAT translates the destination public address to the private address 10.33.96.5 and forwards the packets.
NAPT can be used only for TCP and UDP traffic. In NAPT, multiple private addresses can use a single public address simultaneously. While NAT maps one public address to one private address, NAPT maps the NAPT public address and the public port number to a private address and private port number. Only one NAPT address can be configured for each public address pool.
NAPT is configured simply by specifying one public address or a Dynamic-Address interface (which is using PPP/IPCP to retrieve a public address) that will be used for NAPT traffic. The advantage of NAPT is that it can enable one address from the pool of public IP addresses to support many private IP addresses simultaneously.
Sometimes you may want to configure a station or server in the private network that can be directly accessed from the public network. In this case, you should make a static mapping of the private address of the station to a particular public address. All messages outbound from the private address are translated to the designated public address and all messages inbound for the designated public address are automatically forwarded to the associated private address. There are two kinds of static address mappings: NAT and NAPT.
In a NAT mapping, all IP protocols can access the host. This is
an example of the configuration of a NAT mapping:
| Private address | 10.1.1.2 |
| Private port | 0 |
| Public NAT address | 9.67.1.1 |
| Public port | 0 |
To specify a TCP or UDP application, you have the option to specify a
NAPT mapping that includes a private well-known port. For NAPT static
address mapping, a NAPT public address must be configured. For example,
to configure a Telnet host at private address 10.1.1.1 to
use the NAPT public address 9.67.1.2, the static mapping
would be configured as follows:
| Private address | 10.1.1.1 |
| Private port | 23 |
| Public NAPT address | 9.67.1.2 |
| Public port | 23 |
The private and public ports are mapped to port 23, which is the
well-known port for Telnet. Now, if the administrator also has an FTP
server (well-known address 21) at the same private address
10.1.1.1 to map to the NAPT public address
9.67.1.2, that mapping can look like this:
| Private address | 10.1.1.1 |
| Private port | 21 |
| Public NAPT address | 9.67.1.2 |
| Public port | 21 |
The server at address 10.1.1.1 has the same NAPT public address (9.67.1.2) for both applications, but NAPT can distinguish between the two by using the different port numbers (23 and 21). However, NAPT cannot distinguish between two servers that use the same NAPT public address and have the same application and port number. For example, if the NAPT public address and well-known port are the same for 10.1.1.3 port 21 as for 10.1.1.1 port 21, NAPT cannot tell whether to send incoming FTP traffic to server 10.1.1.3 or 10.1.1.1. To configure more than one server with the same NAPT address and application, you must use a port other than the well-known port at the server (for example, start the FTP daemon on port 200).
In addition to identifying the range of private addresses to be translated by NAT or NAPT, the administrator must set up packet filters and access control rules for IP in the 2212. NAT configuration requires you to configure one inbound and one outbound packet filter on the interface that is connected to the public network. You need to configure one or more access control rules on the inbound packet filter and one or more access control rules on the outbound packet filter. The inbound filter access control rules pass inbound packets with the appropriate defined public addresses to NAT. The outbound filter access control rules pass outbound packets with the appropriate defined private addresses to NAT.
The access control rules that are applied for NAT have the access control rule types I and N for inclusive and NAT. Refer to the Protocol Configuration and Monitoring Reference Volume 1 for information about configuring IP access controls.
| Note: | NAT can also be configured in conjunction with an IPsec tunnel. A sample of this configuration is found in Configuring Packet Filter Access Control Rules for Router A. |
This example shows how to configure NAT for the stub router in the network pictured in Figure 45. See "Configuring and Monitoring Network Address Translator" for descriptions of the commands.
Figure 45. Network Running NAT

Follow this procedure:
NAT config> reserve No 198.76.29.7 255.255.255.0 6 pool1 198.76.29.7 NAT config> reserve No 198.76.29.15 255.255.255.0 3 pool1 0.0.0.0
In this example, a pool called pool1 is established. The NAPT address in the pool is 198.76.29.7. The addresses 198.76.29.13 and 198.76.29.14 are not available, so the pool is set up to exclude them. The parameters entered are: public-address, mask, number-in-group, name, and napt-address. The value 0.0.0.0 for the NAPT address means that none of the addresses in this group is the NAPT address. Use 0.0.0.0 for the NAPT address in all groups if you do not configure NAPT for the pool.
NAT config> translate 10.33.96.0 255.255.255.0 pool1
NAT config> map 10.33.96.5 0 198.76.29.8 0 NAT config> map 10.33.96.4 23 198.76.29.7 23 NAT config> map 10.33.96.4 80 198.76.29.7 80
NAT config> enable NAT
IP Config> add packet-filter outbound out-0 0 IP Config> add packet-filter inbound in-0 0
IP Config>update packet-filter Packet-filter name [ ]? in-0 Packet-filter 'in-0' Config> add access Enter type [E]? IN Internet source [0.0.0.0]? Source mask [255.255.255.255]? 0.0.0.0 Internet destination [0.0.0.0]? 198.76.29.0 Destination mask [255.255.255.255]?255.255.255.0 Enter starting protocol number ([0] for all protocols) [0]? Enable logging? (Yes or [No]): Packet-filter 'in-0' Config>
The range of addresses in the access control rule is greater than the range of addresses defined in pool1. If the address of the packet passed to NAT is in the range defined in the access control rule but is not one of the ones in the public address pool, NAT passes the packet back to IP unchanged.
Packet-filter 'in-0' Config> add access Enter type [E]? I Internet source [0.0.0.0]? 0.0.0.0 Source mask [255.255.255.255]? 0.0.0.0 Internet destination [0.0.0.0]? 0.0.0.0 Destination mask [255.255.255.255]?0.0.0.0 Enter starting protocol number ([0] for all protocols) [0]? Enable logging? (Yes or [No]): Packet-filter 'in-0' Config>
Packet-filter 'out-0' Config> add access Enter type [E]? IN Internet source [0.0.0.0]? 10.33.96.0 Source mask [255.255.255.255]? 255.255.255.0 Internet destination [0.0.0.0]? Destination mask [255.255.255.255]?0.0.0.0 Enter starting protocol number ([0] for all protocols) [0]? Enable logging? (Yes or [No]): Packet-filter 'out-0' Config>
With this packet filter as with filter in-0, you can add a wildcard inclusive access control rule as the last access control rule if you plan to forward packets that do not match the access control rule.
IP Config> set access-control on
NAT> reset NAT IP> reset IP